Introduction to Edge AI in Security Systems

Understanding Edge AI
Edge AI is a revolutionary technology that processes data locally, at the source, rather than sending it to a central server for analysis. This localized processing dramatically reduces latency, enabling faster response times and improved decision-making. In security applications, this immediacy is crucial for reacting to threats swiftly and effectively.
This localized processing also significantly enhances security by minimizing reliance on cloud infrastructure, which can be vulnerable to cyberattacks and data breaches. Edge AI offers a more robust and resilient approach to security, especially in remote or isolated environments.
Data Processing at the Edge
One of the key advantages of edge AI in security is the ability to process data in real-time. This real-time analysis allows security systems to identify and respond to threats as they emerge, rather than waiting for data to be transmitted to a central location. This is particularly important for applications requiring rapid response, such as intrusion detection or surveillance.
Real-Time Threat Detection
Edge AI significantly improves real-time threat detection by enabling the immediate processing of sensor data. This immediate processing allows security systems to identify and respond to threats faster than traditional methods, ultimately reducing the impact of attacks. This speed is paramount in critical security applications where time is of the essence.
Improved Security Through Reduced Latency
The reduced latency associated with edge AI processing is a significant advantage in security applications. By processing data closer to the source, edge AI systems can make decisions and take actions much faster. This is especially important in situations requiring immediate responses, such as preventing intrusions or activating alarms. This reduced latency translates directly into a stronger security posture.
Enhanced Security in Remote Locations
Edge AI is particularly beneficial in remote or isolated security deployments. By processing data locally, these systems can operate independently of central servers, ensuring uninterrupted security even in areas with limited or unreliable internet connectivity. This independence is crucial for maintaining a robust security infrastructure in geographically dispersed environments.
Cost-Effectiveness and Scalability
Edge AI solutions often prove to be more cost-effective in the long run compared to cloud-based solutions, especially for large deployments. By reducing the need for extensive data transmission and processing in the cloud, edge AI systems can significantly lower infrastructure costs. Furthermore, their scalability allows for easy integration into existing security systems and expansion as needed. This makes them adaptable to diverse security environments.
Real-time Threat Detection Capabilities
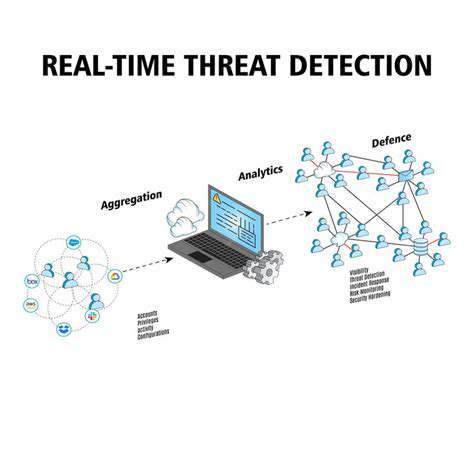
Real-time Threat Detection Capabilities
Real-time threat detection systems are crucial for modern cybersecurity. These systems continuously monitor network traffic and system activity for suspicious patterns that could indicate an impending cyberattack. Rapid identification and response to threats are paramount to minimizing damage and downtime. This proactive approach allows organizations to address potential vulnerabilities before they are exploited, significantly reducing the risk of data breaches and financial losses.
Advanced threat detection capabilities leverage various technologies, including machine learning algorithms and behavioral analytics. These sophisticated tools can identify zero-day exploits and evolving attack vectors that traditional signature-based systems might miss. By analyzing the context and behavior of events, real-time threat detection systems can distinguish legitimate activities from malicious ones, providing a more comprehensive security posture.
Implementing Effective Threat Detection
Implementing an effective real-time threat detection system requires careful consideration of several factors. Organizations need to define clear security policies and procedures that align with their specific needs and risk tolerance. This includes establishing thresholds for alerts and response protocols to ensure timely and appropriate action.
Furthermore, a robust security information and event management (SIEM) system is essential for collecting, analyzing, and correlating security events. This centralized platform provides a comprehensive view of the security landscape, enabling analysts to identify patterns and trends that might indicate ongoing attacks. A well-configured SIEM system is crucial for effective threat hunting and incident response.
Integration and Scalability
Modern threat detection systems must seamlessly integrate with existing security infrastructure. This includes integration with firewalls, intrusion detection/prevention systems (IDS/IPS), and endpoint security solutions. Seamless integration ensures a holistic security approach, preventing information silos and maximizing the effectiveness of the security posture. Without proper integration, it is possible for threats to slip through the cracks, highlighting the critical need for a unified security architecture.
The system must also be scalable to accommodate future growth and increasing volumes of data. This scalability is vital for maintaining effectiveness as organizations expand their operations and data footprint. Scalability is important to ensure that the threat detection system can continue to perform effectively as the network and data volume grow.
Monitoring and Analysis
Continuous monitoring and analysis of threat detection system performance are essential for optimizing its effectiveness. Regular review and adjustment of detection rules and thresholds are necessary to ensure the system remains relevant and responsive to new threats.
Security analysts need access to comprehensive reporting and visualization tools to effectively understand the system's findings. This allows for proactive identification of vulnerabilities and the prioritization of necessary remediation efforts. Thorough analysis of threat data enables more effective responses to real-time threats.