The Impact of Connected Cars on the Automotive Industry

The Rise of Connectivity
Connected cars are rapidly transforming the automotive industry, moving beyond simple entertainment systems to encompass a wide range of functionalities. This integration of technology allows for seamless communication between the vehicle and its surroundings, creating a dynamic and responsive driving experience. The implications of this connectivity extend far beyond the passenger compartment, impacting everything from traffic flow to overall safety.
The shift towards connected car technology is driven by a confluence of factors, including advancements in telecommunications, computing power, and sensor technology. These advancements have enabled the development of sophisticated systems capable of collecting, processing, and transmitting data in real-time. This data-driven approach is revolutionizing how we interact with our vehicles and the world around us.
Enhanced Safety Features
One of the most significant impacts of connected cars is the enhancement of safety features. By connecting vehicles to each other and to infrastructure, real-time information about road conditions and potential hazards can be shared, leading to quicker reaction times and reduced accident rates. This includes features like adaptive cruise control, lane departure warnings, and automatic emergency braking, which are becoming increasingly sophisticated and prevalent in modern vehicles.
Furthermore, connected car technology facilitates the development of advanced driver-assistance systems (ADAS). These systems leverage data from various sources, including other vehicles, traffic signals, and road sensors, to provide drivers with critical information and support, ultimately contributing to a safer and more efficient driving experience.
Improved Efficiency and Convenience
Connected car technology also improves efficiency and convenience for drivers. Vehicle-to-infrastructure (V2I) communication allows for optimized traffic flow, reducing congestion and fuel consumption. This real-time data exchange between vehicles and the surrounding infrastructure can lead to significant improvements in overall traffic management. Furthermore, features like remote vehicle diagnostics and automated parking assist enhance the convenience and usability of the vehicle.
The ability to remotely control various aspects of the vehicle, from climate control to locking/unlocking, adds significant convenience to daily life. This level of control and convenience is particularly beneficial in managing the vehicle from a distance, whether it's checking the status of the vehicle or pre-heating the cabin before arrival.
Data Security and Privacy Concerns
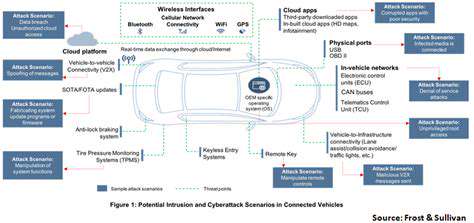
While the benefits of connected cars are substantial, it's crucial to address the inherent security and privacy concerns. The vast amount of data collected and transmitted by connected vehicles raises significant security risks. Hackers could potentially gain access to sensitive information, potentially endangering the occupants and compromising the vehicle's functionality. Robust security measures are essential to protect this data and prevent malicious activities.
Moreover, the privacy implications of data collection must be carefully considered. Concerns about data misuse and unauthorized access to personal information are valid and require careful consideration and appropriate regulations. Transparency and clear guidelines concerning data usage are essential to building trust and ensuring responsible data handling practices.
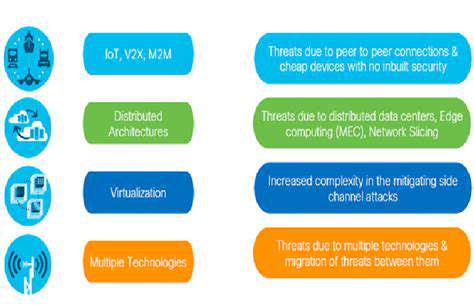
Security Considerations in the Connected Car Ecosystem
Implementing Robust Security Measures
Robust security measures are crucial for protecting sensitive data and systems from unauthorized access, use, disclosure, disruption, modification, or destruction. Implementing these measures requires a multi-faceted approach, encompassing various layers of protection, from network security to data encryption and user authentication. Careful consideration of potential vulnerabilities and threats is paramount in developing effective security strategies. A proactive approach that anticipates and addresses potential weaknesses before they are exploited is essential.
This involves regular security assessments, vulnerability scanning, and penetration testing to identify and mitigate potential risks. Furthermore, staying abreast of emerging threats and vulnerabilities is critical for maintaining a strong security posture. Regular updates and patches for software and systems are essential components of a proactive approach to security.
Data Encryption and Protection
Data encryption is a fundamental security practice that ensures confidentiality and integrity of sensitive information. Using strong encryption algorithms and protocols is vital in safeguarding data at rest and in transit. This includes encrypting data stored in databases, backups, and cloud storage. Proper implementation of encryption protocols is essential to prevent unauthorized access to sensitive information.
Furthermore, robust access controls and secure storage mechanisms are needed to protect data from unauthorized access and modifications. Regular audits and reviews of security controls are also necessary to ensure effectiveness and identify any potential weaknesses or gaps in security practices.
User Authentication and Authorization
Implementing strong user authentication mechanisms is critical for controlling access to sensitive data and systems. This involves verifying the identity of users before granting them access to resources. Multi-factor authentication (MFA) is a strong recommendation to enhance security by requiring multiple forms of identification from users. Strong passwords and the use of MFA are essential for bolstering security and protecting against unauthorized access.
Furthermore, access privileges should be carefully managed and limited to the minimum necessary to perform required tasks. Regular reviews and audits of user access rights are important for maintaining a strong security posture and preventing unauthorized access.
Network Security and Infrastructure
Securing network infrastructure is a critical aspect of overall security. This includes implementing firewalls, intrusion detection systems, and other network security tools to monitor and control network traffic. These tools are essential for identifying and preventing unauthorized access and malicious activity. Proper configuration and maintenance of firewalls and intrusion detection systems are essential for effective network security.
Implementing robust security measures for network infrastructure, such as secure Wi-Fi protocols and VPN connections, is essential for protecting against threats. Regular security audits and penetration testing of network infrastructure are also critical to identify potential vulnerabilities and weaknesses.
Incident Response and Disaster Recovery
Having a well-defined incident response plan is crucial for mitigating the impact of security breaches and other incidents. This plan should outline procedures for detecting, containing, and recovering from security incidents. Developing and testing a comprehensive incident response plan is essential for minimizing the damage and ensuring a swift recovery.
A robust disaster recovery plan is also needed to ensure business continuity in case of major disruptions or disasters. This plan should outline procedures for backing up data, restoring systems, and resuming operations in a timely and efficient manner. Regular testing of the disaster recovery plan is critical for ensuring its effectiveness and minimizing downtime during disruptions.