Post-Quantum Cryptography: Building Resilience
Post-Quantum Cryptography: A Necessary Evolution
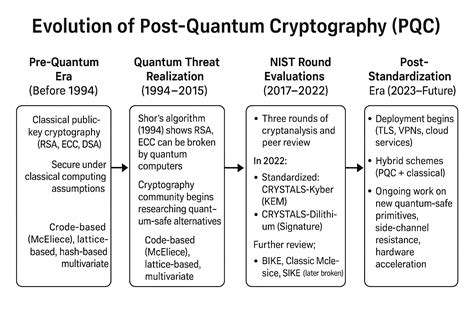
Post-quantum cryptography (PQC) is a crucial development in modern cybersecurity. It addresses the growing threat of quantum computers, which could potentially break many of the encryption methods currently used to protect sensitive data. This emerging field is pivotal in securing our digital future and ensuring the confidentiality and integrity of communications and data storage.
The current encryption standards, largely based on computational problems deemed intractable for classical computers, are vulnerable to attacks from quantum computers. This vulnerability underscores the urgent need for a shift towards PQC to maintain robust security in a post-quantum world.
Understanding the Threat of Quantum Computing
Quantum computing promises to revolutionize various fields, but its potential to break existing cryptographic systems poses a significant threat to digital security. Quantum algorithms, like Shor's algorithm, can efficiently factor large numbers and thus decrypt RSA encryption, a widely used method. This poses a risk to sensitive data, including financial transactions, healthcare records, and national security information.
Key Concepts in Post-Quantum Cryptography
PQC involves developing new cryptographic algorithms resistant to attacks from quantum computers. These algorithms rely on different mathematical problems that quantum computers have not yet found efficient ways to solve.
Several mathematical problems, such as lattice-based cryptography, code-based cryptography, and multivariate cryptography, are being explored as potential foundations for post-quantum algorithms.
Lattice-Based Cryptography: A Promising Approach
Lattice-based cryptography is one of the leading candidates for PQC. It's based on the hardness of certain problems in the mathematical field of lattices, which are sets of points in multi-dimensional space. These problems, unlike factoring or discrete logarithms, are not easily solved by known quantum algorithms.
The inherent complexity of these lattice problems makes them attractive targets for building quantum-resistant encryption schemes. These algorithms are becoming increasingly sophisticated and are showing promising results in various tests and simulations.
Code-Based Cryptography: An Alternative Solution
Code-based cryptography leverages error-correcting codes to create strong cryptographic primitives. These codes, when designed carefully, can provide a robust security against attacks, even from quantum computers.
This approach has some strengths in terms of its theoretical foundation, and it has shown potential for high performance in certain applications.
Multivariate Cryptography: A Less Dominant Approach
Multivariate cryptography relies on systems of multivariate polynomial equations. The difficulty in solving these systems is the foundation for security. However, compared to other candidates, it has faced some challenges in terms of performance and implementation.
The Future of Post-Quantum Cryptography
The transition to PQC is an ongoing process. Governments and organizations are actively involved in standardizing and implementing these new cryptographic algorithms. This transition requires careful consideration of various factors, including security analysis, performance evaluation, and practical deployment.
The future of secure communication and data protection rests heavily on the successful adoption of post-quantum cryptography.
The Role of Quantum-Resistant Algorithms in Cybersecurity
Quantum Computing's Threat to Current Cryptography
The advent of quantum computing poses a significant threat to the security of widely used cryptographic systems. Current public-key cryptography, the cornerstone of internet security, relies on mathematical problems considered intractable for classical computers. However, powerful quantum computers, capable of exploiting quantum phenomena like superposition and entanglement, could potentially solve these problems in a fraction of the time it would take a classical computer, rendering current encryption vulnerable.
This vulnerability extends beyond financial transactions and online communications. Sensitive government data, medical records, and intellectual property are all protected by encryption methods susceptible to quantum attacks. The potential for widespread breaches of security is substantial, necessitating proactive measures to safeguard against this emerging threat.
Understanding Quantum Algorithms
Quantum algorithms are fundamentally different from classical algorithms. They leverage the unique properties of quantum mechanics to solve problems in ways classical computers cannot, particularly in areas of optimization and searching. Algorithms like Shor's algorithm, designed to efficiently factor large numbers, and Grover's algorithm, used for searching unsorted databases, are of particular concern in the context of cybersecurity.
While the theoretical underpinnings of these algorithms are complex, the core concept centers on exploiting quantum phenomena to perform calculations in parallel, drastically accelerating the speed of computation compared to classical methods. This parallel processing power is what makes them a threat to current encryption methods.
The Need for Quantum-Resistant Cryptography
The potential for quantum computers to break existing cryptographic systems necessitates a proactive and urgent transition to quantum-resistant cryptography. This isn't just a theoretical concern; it's a practical necessity for maintaining the security of digital infrastructure in the face of an emerging technological threat. Ignoring this challenge could have catastrophic consequences for online security and privacy.
Types of Quantum-Resistant Algorithms
A diverse range of quantum-resistant algorithms are under development, each addressing different cryptographic challenges. These algorithms often rely on new mathematical problems that are believed to be intractable for both classical and quantum computers. Examples include lattice-based cryptography, code-based cryptography, multivariate cryptography, and hash-based cryptography, each with its own strengths and weaknesses.
Current Research and Development
Significant research and development efforts are underway to explore and refine quantum-resistant algorithms. Cryptographic standards organizations and academic institutions are actively working to define and implement new cryptographic protocols and standards. This continuous development ensures that the transition to quantum-resistant cryptography is a gradual and well-supported process, reducing the impact on existing systems and minimizing disruption.
Challenges in Implementing Quantum-Resistant Cryptography
Despite the importance and urgency, the transition to quantum-resistant cryptography presents several challenges. These include the need for new hardware and software infrastructure, the potential for compatibility issues with existing systems, and the potential for implementation errors that could compromise security. Furthermore, the complexity of some quantum-resistant algorithms introduces a new level of scrutiny in terms of security audits and verification.
The Future of Cybersecurity in the Quantum Era
The development and adoption of quantum-resistant cryptography represent a critical step in safeguarding against the looming threat of quantum computing. The future of cybersecurity in the quantum era hinges on collaborative efforts between researchers, industry leaders, and policymakers. A concerted effort to understand, develop, and implement quantum-resistant algorithms will be essential to maintaining the integrity and security of our digital world as quantum computing capabilities continue to advance.
Challenges and Future Directions in Quantum Cybersecurity
Quantum Algorithm Development for Cybersecurity Threats
The development of quantum algorithms poses a significant threat to existing cryptographic systems. Understanding and mitigating these threats requires a proactive approach to algorithm development, focusing on both offensive and defensive strategies. Researchers must not only explore quantum algorithms capable of breaking current encryption methods but also develop countermeasures that can withstand these attacks. This includes investigating post-quantum cryptography (PQC) and exploring novel approaches to quantum-resistant encryption schemes. This research is crucial for maintaining the security of sensitive data in the face of emerging quantum computing capabilities.
Analyzing the potential vulnerabilities of various cryptographic protocols to quantum algorithms is essential. This requires a deep understanding of the underlying mathematical structures and the specific computational resources needed to execute these algorithms. Careful consideration must be given to the practical implications of quantum computing capabilities, such as the size and speed of future quantum computers, and how this impacts the feasibility and effectiveness of different attack strategies. This analysis will inform the development of robust defense mechanisms.
Quantum-Resistant Cryptography (PQC) Implementation and Standardization
Post-quantum cryptography (PQC) is a crucial area of research aimed at developing cryptographic algorithms resistant to attacks from quantum computers. The standardization process for PQC algorithms is complex, requiring rigorous testing, validation, and interoperability considerations. This process must ensure that selected algorithms are secure, efficient, and suitable for practical implementation across different platforms and applications. A key challenge lies in achieving a balance between security and practicality, ensuring that PQC algorithms are not overly resource-intensive and can be implemented in real-world systems.
Implementing PQC algorithms into existing systems and protocols requires careful consideration. Migrating from current cryptographic standards to PQC algorithms will necessitate significant changes in software, hardware, and infrastructure. The transition must be managed carefully to avoid disruptions in communication and data security. Educating developers and users about the new standards is essential for a smooth and successful deployment of PQC.
Quantum Computing Infrastructure and Resource Management
The availability and accessibility of quantum computing resources will play a critical role in shaping the future of quantum cybersecurity. Developing and maintaining robust quantum computing infrastructure, including hardware and software, is essential for both researchers and practitioners. This includes considerations for scalability, reliability, and cost-effectiveness, as well as the development of efficient resource management strategies to optimize the use of quantum computing capabilities for cybersecurity tasks.
Understanding the limitations and potential vulnerabilities of quantum computing infrastructure is paramount. Researchers need to evaluate the security of quantum hardware and software, and protocols for secure access to quantum resources. This involves addressing issues like potential side-channel attacks, ensuring the integrity of quantum algorithms, and preventing unauthorized access to sensitive data and computational resources.
Ethical and Societal Implications of Quantum Cybersecurity
The implications of quantum computing on cybersecurity extend beyond technical challenges. Ethical considerations surrounding the development and deployment of quantum-resistant technologies are crucial. Issues like data ownership, privacy, and the potential for misuse of quantum capabilities must be addressed proactively. Developing ethical guidelines and regulations for the responsible use of quantum computing in cybersecurity is essential for mitigating potential risks and ensuring that the technology benefits society as a whole.
The potential impact on various societal sectors, such as finance, healthcare, and government, needs careful consideration. Understanding the potential disruptions and adapting existing frameworks to accommodate new quantum-based threats is crucial. This will require collaboration between researchers, policymakers, and industry stakeholders to address the evolving challenges in a comprehensive and proactive manner.