Key Benefits of Edge Computing in Industrial IoT Analytics
Enhanced Performance and Responsiveness
Edge computing significantly improves application performance by processing data closer to the source. This proximity minimizes latency, leading to quicker response times for applications requiring real-time interaction, such as video streaming, gaming, and industrial automation. This reduced latency translates directly into a more seamless and engaging user experience. Furthermore, by offloading tasks to edge devices, the burden on central servers is lessened, leading to greater overall system efficiency.
The reduced latency also contributes to improved user experience in applications like video conferencing and online gaming, leading to smoother interactions and fewer disruptions. This closer proximity of processing to the data source allows for faster data processing and reduces the time needed to deliver the data to the user, leading to a superior user experience.
Improved Reliability and Resilience
Edge computing fosters a more resilient system architecture by distributing data processing across multiple locations. This distribution reduces dependence on a single point of failure, such as a central data center. If a portion of the network experiences disruptions, edge devices can continue to operate independently, ensuring uninterrupted service. This redundancy is crucial in mission-critical applications where downtime is unacceptable.
Furthermore, edge computing enhances the overall reliability of applications by minimizing the impact of network congestion or outages. Data processing closer to the source reduces the reliance on the central network, making the system more robust and less susceptible to disruptions. This redundancy is crucial in many applications, especially those requiring continuous operation, like industrial automation.
Reduced Network Congestion and Costs
By processing data closer to the source, edge computing significantly reduces the volume of data transmitted across the network. This reduction in network traffic translates into lower bandwidth costs and improved network performance. This is particularly valuable in scenarios with limited or expensive network infrastructure, such as remote locations or areas with high data traffic.
Edge computing also lowers communication costs by reducing the amount of data that needs to be transferred across the network. This is especially important for applications that generate a large volume of data, such as IoT devices and sensor networks. This reduction in network traffic also translates to reduced energy consumption, further lowering operational costs.
Enhanced Security and Privacy
Edge computing offers enhanced security by processing sensitive data locally. By keeping sensitive information closer to the source, edge devices can apply local security measures and encryption, minimizing the risk of data breaches during transmission to a central server. This approach is especially important for applications handling confidential information, like financial transactions and healthcare data.
Local processing also allows for more granular control over data access and usage, enhancing privacy. This is particularly critical in industries like healthcare and finance, where stringent data privacy regulations are in place. The ability to process data closer to the source gives organizations more control over data security and compliance.
Discomfort often serves as a catalyst for personal development, pushing individuals beyond their comfort zones. When faced with challenges, people are compelled to adapt, learn, and evolve. This transition is pivotal in fostering resilience, contributing to a more enriched and robust character.
Addressing Security and Data Management Challenges
Ensuring Data Integrity
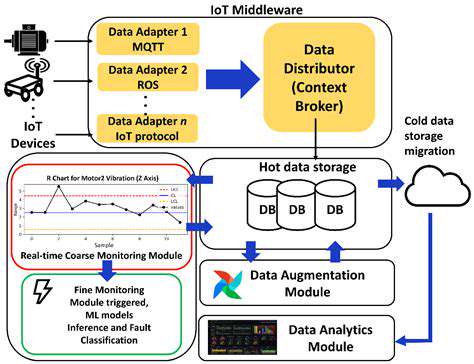
Data integrity is paramount in industrial IoT (IIoT) applications, where real-time data accuracy directly impacts operational efficiency and safety. Edge computing plays a crucial role in ensuring this integrity by processing data locally, minimizing latency, and reducing the risk of data corruption during transmission to the cloud. By validating data at the edge and performing initial analysis, we can identify anomalies and potential issues early on, preventing them from propagating through the system and potentially causing widespread disruptions.
Implementing robust data validation and checksumming mechanisms at the edge can further enhance data integrity, ensuring that only reliable and accurate information is used for decision-making. This localized validation process also reduces the volume of data transmitted to the cloud, thereby lowering bandwidth requirements and associated costs.
Securing Edge Devices
The proliferation of edge devices in industrial settings necessitates robust security measures to protect sensitive data from unauthorized access and malicious attacks. Implementing strong authentication protocols, encryption methods, and intrusion detection systems at the edge is critical to prevent compromise of the entire IIoT ecosystem. These security measures should be tailored to the specific vulnerabilities and threats associated with each edge device and its environment.
Regular security audits and vulnerability assessments are essential to identify and address potential security gaps in edge devices. Patches and updates should be applied promptly to mitigate known vulnerabilities as they are discovered, ensuring that the edge infrastructure remains secure and resilient.
Managing Data Volume and Velocity
Industrial IoT applications often generate massive amounts of data at high velocity. Traditional cloud-based architectures can struggle to handle this volume and velocity, leading to performance bottlenecks and data loss. Edge computing allows for the processing and filtering of data at the source, significantly reducing the load on the central cloud infrastructure. This localized processing also enables faster response times to critical events, which is especially crucial in time-sensitive industrial applications.
Protecting Sensitive Information
Many industrial IoT applications handle sensitive data related to production processes, equipment health, and personnel safety. Securing this sensitive data is critical to maintaining operational confidentiality and compliance with data protection regulations. Edge computing enables the encryption and secure storage of data at the edge, minimizing the risk of data breaches during transmission to the cloud. This localized approach also allows for compliance with data residency requirements, ensuring that sensitive data is stored within designated geographical boundaries.
Addressing Latency and Reliability Concerns
In industrial environments, real-time data processing is essential for efficient operations. Cloud-based architectures can introduce significant latency, impacting decision-making and potentially jeopardizing safety. Edge computing, by processing data locally, significantly reduces latency, enabling faster responses to critical events and improving overall system reliability. Robust edge infrastructure with redundant components and failover mechanisms further enhance the reliability of data processing and system uptime.