Quantum Key Distribution (QKD): The Fundamentals
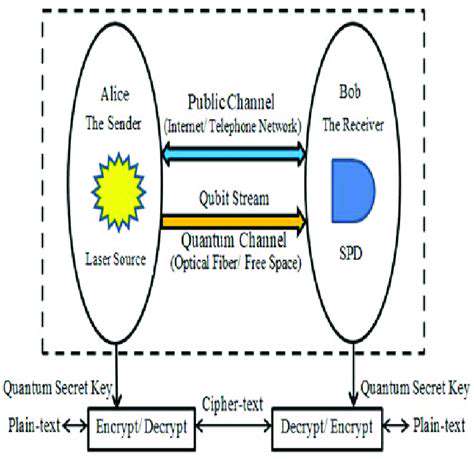
Quantum Key Distribution (QKD) is a revolutionary approach to secure communication that leverages the principles of quantum mechanics. It offers the potential for unconditionally secure communication, a feat not achievable with any classical cryptographic method. This is because any attempt to eavesdrop on a QKD-protected channel will inevitably disturb the quantum system, alerting the legitimate users to the intrusion.
The core principle behind QKD lies in the fundamental laws of quantum mechanics, particularly the Heisenberg Uncertainty Principle. This principle dictates that certain pairs of physical properties of a quantum system, like position and momentum, cannot be simultaneously known with perfect accuracy. This inherent unpredictability forms the bedrock of QKD's security.
Quantum States and Entanglement
QKD systems rely on the transmission of specific quantum states, often photons, which are fundamental particles of light. These photons are carefully prepared to carry information in the form of polarization or phase, representing bits of data.
Entanglement is a crucial element in many QKD protocols. Entangled photons share an intrinsic connection, meaning that measuring a property of one entangled photon instantaneously reveals the corresponding property of the other, regardless of the distance separating them. This interconnectedness is exploited to generate and distribute secret keys.
Key Distribution Protocols
Several QKD protocols exist, each with its own strengths and weaknesses. These protocols often employ different quantum states and measurement techniques to achieve secure key distribution.
BB84, a widely studied protocol, utilizes polarization states of photons. It is comparatively simple to implement and has been successfully demonstrated in various scenarios. Other protocols, such as the E91 protocol, utilize more sophisticated quantum states and techniques to achieve higher levels of security and efficiency.
Security Aspects and Challenges
The security of QKD stems from the inherent unpredictability of quantum mechanics. Any attempt to intercept or measure the transmitted quantum states will inevitably alter them, leaving a detectable signature. This makes it practically impossible for an eavesdropper to gain access to the secret key without being detected.
However, QKD systems still face challenges, such as channel loss and noise. The transmission of photons over long distances is susceptible to attenuation and disturbance, requiring advanced techniques to mitigate these effects and maintain the security and integrity of the quantum channel.
Practical Implementations and Applications
QKD systems are becoming increasingly sophisticated, with practical implementations emerging in various fields. Secure communication in financial transactions, government communications, and critical infrastructure are potential applications, leveraging the inherent security advantages of QKD.
While still in its early stages of widespread adoption, QKD holds immense promise for future communications. Continuous research and development are driving innovation in QKD technology, leading to more robust and efficient systems capable of handling increasingly demanding security requirements.
Future Directions and Research
Future research in QKD focuses on increasing the range and efficiency of quantum key distribution. Developing more robust and reliable protocols for overcoming channel losses and noise is a key area of investigation.
Improved system design and integration with existing communication infrastructures are vital for widespread adoption. Furthermore, exploring new quantum states and measurement techniques promises to enhance security and performance, paving the way for more secure and reliable communication networks.
Challenges and Future Directions of Quantum Cryptography
Key Challenges in Implementing Quantum Cryptography
One of the primary hurdles in the practical application of quantum cryptography lies in the development of robust and scalable quantum key distribution (QKD) systems. Current QKD technologies often face limitations in terms of transmission distances, especially over fiber optic cables, which can be affected by atmospheric disturbances. These limitations necessitate the use of specialized repeater technologies, which are still under active development and pose significant engineering challenges. Moreover, the high cost of the necessary quantum components like single-photon detectors and entangled photon sources presents a considerable barrier to widespread adoption.
Another critical challenge is ensuring the security of QKD systems against potential attacks. While quantum mechanics inherently provides a level of security, adversaries could potentially exploit vulnerabilities in the implementation or the underlying infrastructure. Sophisticated attacks targeting the quantum channels or the components used in the QKD system are a constant concern for researchers, and ongoing efforts are needed to develop robust countermeasures to these potential threats.
Quantum Key Distribution Protocols and Their Limitations
Various quantum key distribution protocols, such as BB84 and E91, are currently employed. These protocols rely on the fundamental principles of quantum mechanics to establish a shared secret key between two parties. However, each protocol has its own set of limitations. For instance, BB84, while widely used, may suffer from efficiency issues in noisy channels, while E91 requires more sophisticated hardware. Further research into new protocols and their optimization is crucial for enhancing the performance and practicality of QKD systems.
The inherent complexity of implementing quantum protocols, especially in real-world scenarios, is a significant limitation. The need for precise control over quantum systems and the susceptibility to noise and errors during transmission are crucial factors that require careful consideration in the design and operation of QKD systems. The ongoing quest for more robust and efficient protocols is a major area of research in quantum cryptography.
Scalability and Integration with Existing Infrastructure
A significant future direction for quantum cryptography is to scale QKD systems to meet the demands of large-scale communication networks. This involves extending the transmission distances, increasing the key generation rates, and integrating QKD with existing optical fiber infrastructure. This integration is essential to avoid the need for completely new communication channels. Successfully integrating QKD into existing telecom networks is a crucial step in making quantum cryptography a viable technology for broad deployment.
The cost-effectiveness of QKD systems is another important consideration. Research and development efforts are focused on lowering the cost of quantum components and improving the efficiency of QKD protocols. Only by reducing the financial burden can quantum cryptography gain wider adoption and become a practical solution for secure communication.
Security Against Advanced Attacks
Quantum cryptography, while inherently secure against eavesdropping, is not invulnerable. Sophisticated attackers could potentially exploit vulnerabilities in the implementation of QKD systems, or develop novel attack strategies that exploit the nuances of quantum mechanics. Researchers are constantly working to develop countermeasures against these advanced attacks, which require a nuanced understanding of quantum mechanics and advanced mathematical tools. For example, the development of quantum-resistant cryptography is an active area of research to ensure security in the face of future quantum computing advancements.
Maintaining the security of quantum channels is paramount. The development of techniques to detect and mitigate attacks, such as those based on side-channel analysis or quantum hacking, is essential to ensure the reliability and trustworthiness of quantum cryptographic systems. Future research should focus on developing robust and adaptable security mechanisms to protect against emerging threats and future advancements in quantum computing technologies.
Future Directions and Emerging Applications
The future of quantum cryptography promises exciting developments in various applications beyond secure communication. The integration of QKD with other quantum technologies, such as quantum computing and quantum sensing, could lead to innovative applications in areas like secure distributed quantum computation and ultra-precise measurements. Researchers are exploring applications in financial transactions, secure cloud storage, and other sensitive data handling scenarios.
Further research is needed to explore the possibility of quantum cryptography in satellite-based communication systems. This could open up new avenues for secure global communication networks and enable secure communication in space. Exploring these novel applications will expand the reach and impact of quantum cryptography, creating an even more secure digital future.